Cyber attacks have become a mounting threat to the pharmaceutical industry over the past year, putting COVID-19 research data as well as supply and distribution chains at risk. We explore what can pharma learn from more experienced industries as they try to mitigate hacking
Danny Buckland
The breakthrough genome sequencing of COVID-19 and rapid creation of vaccines has thrust science and the pharmaceutical industry into the global spotlight. By doing this however, regretfully it has also positioned it directly in the crosshairs of organised crime and state-sponsored disruption.
The industry is contending with unprecedented levels of cyber-attacks; hackers on the hunt for vaccine research data. As well as this, the potential of supply theft across pharma’s development and distribution chain is under threat.
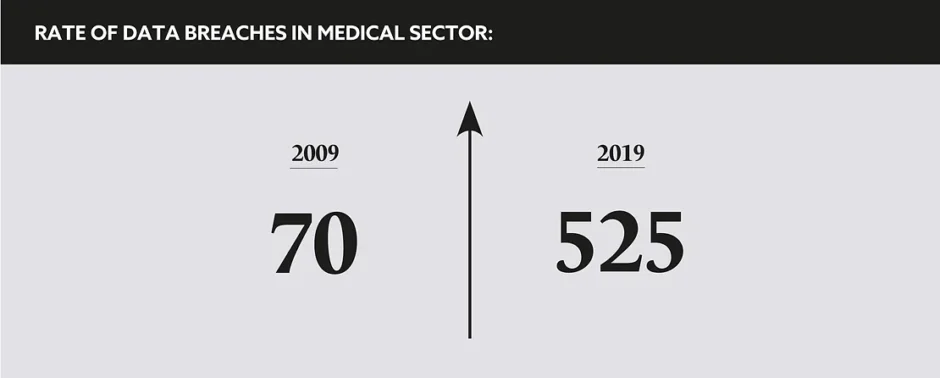
“As Europe’s health system is being pushed to the limit, responding to cyber-attacks has become an almost insurmountable challenge to face,” claims The European Union Agency for Cybersecurity. ENISA’s Threat Landscape Report cited a concerning 667% increase in phishing attacks within just one month of the pandemic. In addition to this, both the WHO and the FBI have warned about fraudulent communications, discussing infection rates and medical opinions, disguised so as to appear legitimate and ‘official’.
These carefully constructed scams risk exploiting system vulnerabilities, and plenty of other major organisations have fallen victim to the problem of hacking. The European Medicines Agency revealed in December that it was a target of a cyber-attack attempting to snare details of the Pfizer/ BioNTech COVID-19 vaccine. The agencies Interpol and Europol have also cautioned against an ‘onslaught’ of criminal activity linked to vaccines, ranging from online fraud and cyber-crime to theft and counterfeiting.
Unprecedented risk
Pharma companies are by now well-versed in resisting commercial threats and fighting fake medicine, but its defences have never been tested like this before. Cyber criminals, individual disruptors, and state-sponsored operations have been continually probing for weak links along the entire perimeter of healthcare. By nature of healthcare systems using unique platforms and protocols, sometimes crudely bolted together, each contact point or join is a potential back door.
Pharma are not the only ones at risk. “Healthcare is a vast, complex, and fragmented ecosystem and as the sector digitalises itself, it exposes itself to cybersecurity challenges,” says Dr Evangelos Ouzounis, Head, ENISA’s Secure Infrastructure and Services Unit. Public hospitals and healthcare organisations are particularly vulnerable as they have legacy IT systems and cannot afford staff specifically dedicated to repelling cyber-attacks.
“They are scientific-oriented companies that are used to collaborating and sharing,” adds Dr Ouzounis. “They know patents and IPR and are very good at protecting them, but they are not necessarily very good at data protection and having appropriate security in their networks. The big companies will invest to protect themselves but there is risk.”
A robust response
A robust response is required. Research by cyber security experts Blue Voylant reveal that attacks on pharma companies rose by 50% in 2020 compared to the year prior. Stealing data to create a black-market vaccine operation is a factor, but data hackers are even obtaining employee credentials to target shipments and hijack supplies of virus-testing kits and phials of the vaccine that are being delivered. Thorsten Neumann, President and CEO, Transport Asset Protection Association reiterates: “We need to tell people at the vaccine centres that they carry gold.”
ENISA has been working to raise awareness and promote the sharing of information across private and public organisations to stiffen resilience in healthcare systems against growing cyber threats. It also provides appropriate practices on cybersecurity so that breaches can be contained going forward.
The guidance includes basic safety responses, such as educating staff about the threat from malicious emails, warning of the dangers in over-sharing personal information, and beefing up security filters and applying machine learning programmes that can identify phishing sites in real-time.
The World Economic Forum also released a string of defensive tactics including network segmentation to isolate attacks and closer management of third parties such as suppliers, vendors or collaborators that might have weaker cybersecurity protocols. It also advocated developing resilience playbooks to establish fast responses if systems are breached.
“Healthcare can learn a lot from sectors like finance and telecoms, where almost all assets are virtual, and they have invested heavily in cybersecurity,” concludes Dr Ouzounis. “It will be another difficult year, but the good thing is that pharmaceutical companies know they are targets and are responding. Because the vaccination is critical to a well-functioning society and economy, governments are going to protect it and prioritise cyber security.”
Healthcare is a vast, complex and fragmented ecosystem and as the sector digitalises itself, it exposes itself to cybersecurity challenges